Monday, July 22, 2024 11 min read Cybersecurity
The Importance of Penetration Testing in Cybersecurity

Cybersecurity is more crucial with the rise of cyber-attacks and data breaches. Organizations are facing unique threats to their sensitive information and systems. One of the most effective ways to protect against these threats is through penetration testing, also known as pen testing or penetration testing.
What is Penetration Testing?
Penetration testing is a simulated cyber-attack against a computer system, network, or web application to assess its security vulnerabilities. Unlike vulnerability scanning, which only identifies potential vulnerabilities, penetration testing attempts to exploit these vulnerabilities to determine the severity of the risk.
There are several types of penetration testing:
- Network
- Web application
- Social engineering
- Wireless testing.
The penetration testing process typically involves planning, execution, and reporting, with the goal of identifying vulnerabilities and providing recommendations for remediation.
Why the Need Penetration Testing?
As technology becomes increasingly intertwined with people's lives and business operations, the threat of cyber-attacks grows in tandem. Even high-profile companies have fallen victim to these attacks, resulting in costly data breaches. To mitigate these risks, Penetration Testing is essential. Here’s why your company needs it
Here is how and why Penetration Testing is crucial for your company:
- Penetration Testing helps uncover vulnerabilities within the company’s digital infrastructure before attackers can exploit them.
- Regulatory frameworks like HIPAA, PCI-DSS, and GDPR require regular penetration testing to safeguard sensitive data. Compliance not only protects the company from legal repercussions but also ensures trust among stakeholders.
- Penetration testing shields the company from significant financial losses and disruptions to operations by preventing successful cyber-attacks through pre-emptive vulnerability assessments.
- Regularly conducting penetration testing demonstrates the company’s commitment to maintaining high security standards. This commitment is crucial for fostering customer trust and loyalty, as it shows proactive measures are in place to protect their data.
- Penetration testing enhances the company's incident response capabilities by simulating attack scenarios. This process provides valuable insights that enable effective mitigation and management of security incidents as they arise.
- Incorporating penetration testing into the company’s cybersecurity strategy not only safeguards your company against evolving threats but also reinforces your commitment to protecting both your assets and your stakeholders' interests.
Benefits of Penetration Testing
Penetration testing offers numerous benefits, including:
- Identification of vulnerabilities and weaknesses: Penetration testing helps identify vulnerabilities and weaknesses that attackers could exploit.
- Prioritization of remediation efforts: By identifying the most critical vulnerabilities, organizations can prioritize remediation efforts and allocate resources more effectively.
- Compliance with regulatory requirements: Many regulatory requirements, such as HIPAA and PCI-DSS, mandate penetration testing as part of an organization's security protocol.
- Penetration testing can help organizations avoid the financial and reputational costs of a cyber-attack.
- Improved incident response and disaster recovery planning: Penetration testing can help organizations develop more effective incident response and disaster recovery plans.
- Enhanced security posture and reputation: By prioritizing penetration testing, organizations can demonstrate their commitment to security and enhance their reputation.
Common Misconceptions About Penetration Testing
There are several common misconceptions about penetration testing that can prevent organizations from prioritizing it:
- Many believe that penetration testing is too expensive or time-consuming, however, the cost of penetration testing is reduced by the potential cost of a cyber-attack.
- Another misconception is that pen testing is only necessary for large organizations. An organization handles sensitive information or has an online presence, which is at risk for cyber-attacks, so pen testing is for all businesses.
Best Practices for Implementing Penetration Testing
To get the most out of penetration testing, organizations should:
- Conduct regular penetration testing: Penetration testing should be conducted regularly to ensure that new vulnerabilities are identified and remediated.
- Choose a qualified penetration testing provider: Organizations should choose a provider with experience and expertise in penetration testing.
- Integrate penetration testing into existing security protocols: Penetration testing should be integrated into an organization's existing security protocols to ensure that vulnerabilities are identified and remediated in a timely manner.
- Prioritize remediation and vulnerability management: Organizations should prioritize remediation efforts based on the severity of the vulnerabilities identified during penetration testing.
How Penetration Testing is Done: Use Case
There are several scenarios in which a penetration test is necessary. For instance, when deploying a new application or system, it's essential to test its security before it goes live. Similarly, after making significant changes to an existing system, a pen test can help identify any new vulnerabilities that may have been introduced.
If your organization has experienced a security incident or breach, a pen test can help identify the root cause and prevent future occurrences. Additionally, many regulatory requirements, such as HIPAA and PCI-DSS, mandate regular penetration testing to ensure compliance.
The Penetration Testing Process
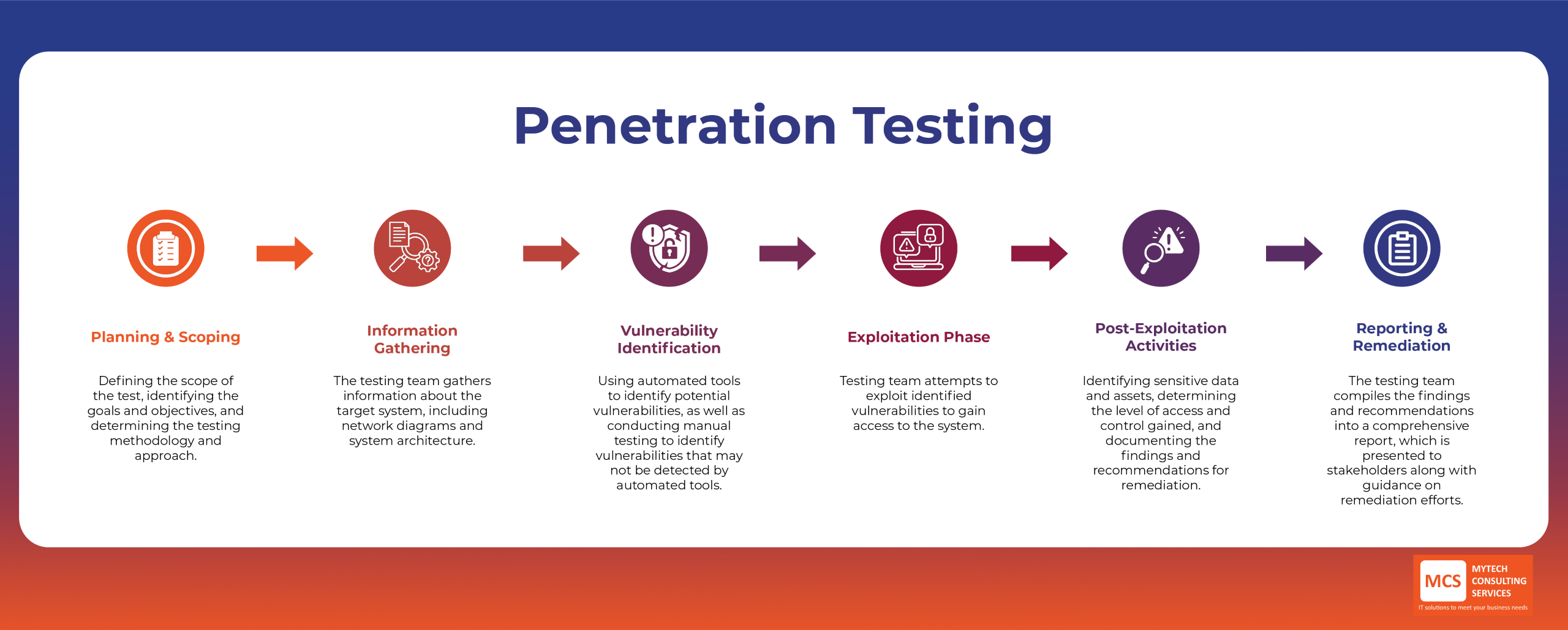
The penetration testing process typically begins with planning and scoping. This involves defining the scope of the test, identifying the goals and objectives, and determining the testing methodology and approach.
The next step is information gathering, where the testing team gathers information about the target system, including network diagrams and system architecture. They may also conduct reconnaissance to identify potential entry points and use tools and techniques to gather information.
Once the information gathering phase is complete, the testing team moves on to vulnerability identification. This involves using automated tools to identify potential vulnerabilities, as well as conducting manual testing to identify vulnerabilities that may not be detected by automated tools. The results are then analysed to identify potential entry points and vulnerabilities.
The exploitation phase is where the testing team attempts to exploit identified vulnerabilities to gain access to the system. They may use various techniques to escalate privileges and move laterally within the system, documenting the steps taken to exploit the vulnerabilities.
After gaining access to the system, the testing team conducts post-exploitation activities, analysing the system to identify sensitive data and assets, determining the level of access and control gained, and documenting the findings and recommendations for remediation.
The final step in the penetration testing process is reporting and remediation. The testing team compiles the findings and recommendations into a comprehensive report, which is presented to stakeholders along with guidance on remediation efforts. The organization then works to implement the recommended remediation efforts, and the testing team verifies that the fixes have been successful.
The Benefits of Penetration Testing
Conducting a penetration test provides numerous benefits to an organization.
- It identifies vulnerabilities and weaknesses in the system by providing a comprehensive understanding of its security posture.
- It prioritizes comprehensive efforts by ensuring the most critical vulnerabilities are addressed first; and
- It meets compliance and regulatory requirements by enhancing the overall security of the system and organization.
Conclusion
In conclusion, penetration testing is a crucial aspect of cybersecurity that helps organizations identify vulnerabilities and prevent cyber-attacks. By prioritizing penetration testing, organizations can avoid the financial and reputational costs of a cyber-attack, improve their incident response and disaster recovery planning, and enhance their security posture and reputation. Don't wait until it's too late – make penetration testing a priority in your organization's cybersecurity strategy today.
Protect Your Organization's Cybersecurity with MYtech's Penetration Testing Services
MYtech Consulting Services and iCT Group offer a comprehensive IT solution service that includes advanced cybersecurity solutions. Our team of experts will work with you to design a customized penetration testing plan that identifies vulnerabilities and provides recommendations for remediation. With our partnership, we can provide a comprehensive solution that includes infrastructure support, ongoing maintenance, and advanced cybersecurity solutions.
Why Choose MYtech?
- Single point of contact for all your IT needs
- Expertise in penetration testing and cybersecurity
- Customized penetration testing plans
- Ongoing maintenance and support
Don't wait until it's too late!
Contact MYtech today to learn more about our penetration testing services and how we can help protect your organization's cybersecurity. Reach out to us at www.mytechcs.com to schedule a consultation and take the first step in protecting your organization's sensitive information and systems.